Data Recovery From Ransomware, WannaCry, CTB Locker, Locky, Crypto Locker, Crypto Wall
CTB Locker virus (Curve Tor Bitcoin Locker, Locky, Crypto Locker, Crypto Wall) or Critroni is a virus that encrypts files. It demands payment for the user to decrypt the data. Hence the name “ransomware” or “ransom Software”. This software first appeared on Windows operating systems, in mid-July 2014.
CTB Locker virus encrypts not all data on the hard disk
This virus does not always encrypt the entire hard drive. Automatic backups, old versions of files that are still on the hard drive, and other system files are not included in the encryption. Stellar Data Recovery has extensive experience in recovering the encrypted data and has already helped many people in retrieving their most important documents.
Contact Stellar for CTB Virus Recovery
Please contact Stellar Ransomware Removal service for CTB Virus Recovery. Our engineers and experts have over 20 years of experience.
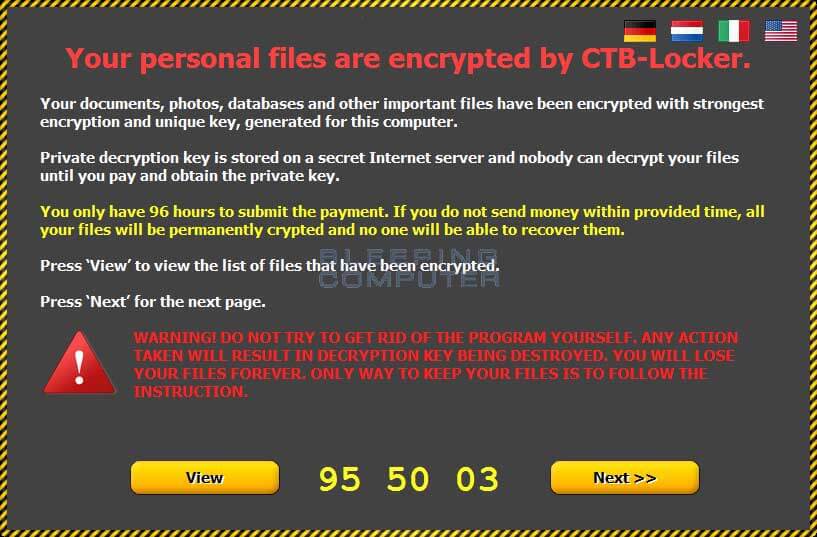
Do not pay ransom

Security experts, police, and government agencies recommend not to pay the ransom. Even after payment, the files do not get decrypted, in addition to this, you support the cyber hackers by paying in bitcoins.
Do not open suspicious emails
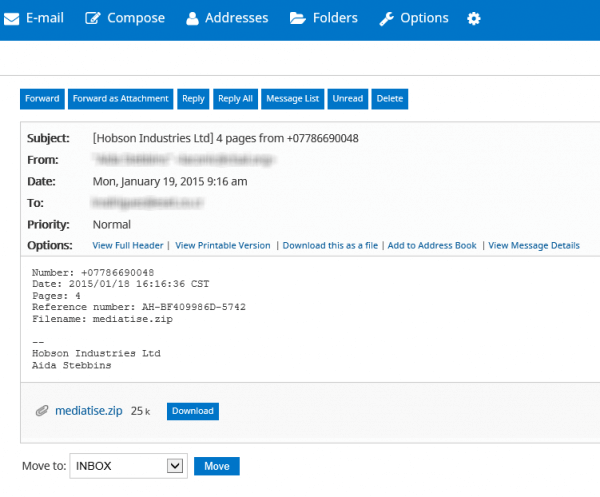
Emails are the most common way for the hackers to gain access to the victim’s system. Once the link is open by the unsuspected user, the virus spreads its claws on the system. An example of a fake email.
Do & Dont’s for CTB virus recovery
Ransomware attacks are becoming common these days, and the hackers are making new versions of ransomware, more powerful and destructive than its predecessors. The latest ransomware versions encrypt the file’s or data on your PC making it inaccessible and demanding money to restore the data. Ransomware can reach your PC from any sources which include:
- Visiting suspicious, unsafe or fake websites
- Opening Emails for unknown sender
- Clicking on unreliable links on Social Media sites
Therefore, we advise our customers to follow these rules.
- Not to open unknown email
- Never visit a suspicious website
- Always update windows os and software
- Maintain a backup of the data on external hard drive or cloud storage
- Use an Anti Virus Software
- Use two-factor authentication
- Most of all Encrypt sensitive data
Following the above can protect your valuable & sensitive data from the hacker.




